Intro
Reconnaissance, assets discovery, attack surface mapping, subdomains discovery… the initial step in a pentesting or bug hunting assessment is one of the most important and will help you find those sites that nobody found before. The more assets you find, the more attack surface you have, which translates into more potential vulnerabilities, apart from some unique vulnerabilities related to hidden assets and this is where reconFTW comes in.
ReconFTW
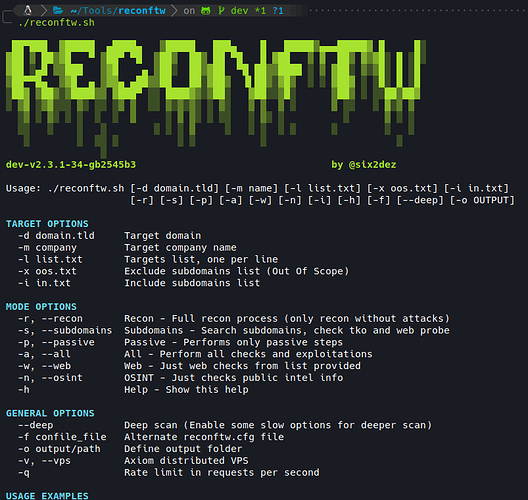
Sticking to its official description, reconFTW (stands for recon For The Win) is a tool designed to perform automated recon on a target domain by running the best set of tools to perform scanning and finding out vulnerabilities.
In other words, given a target domain (or domains), it puts special effort into enumerating subdomains, performing different discovery techniques to subsequently perform a unique workflow/methodology that provides it with an incredible amount of information about its target in order to have everything ready to start with the exploitation phase.
ReconFTW’s main menu
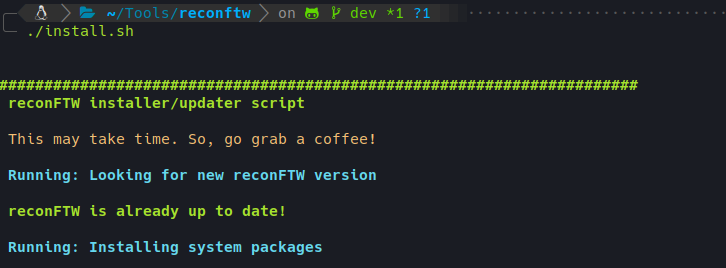
In addition, it has an installer that easily configures a complete environment for pentesting, installing more than 50 tools ready to work. This installer also serves as a reconFTW updater, detecting if there is a new version and downloading it.
Installer running
The steps performed one by one at a high level are described below.
OSINT
Although not the main objective of the tool, this phase provides some information that may be useful in more advanced stages of the audit.
- Basic domain information such as whois, registrant, etc.
- Google and GitHub dorking.
- Metadata on indexed public documents (authors, software, etc.).
- Search for emails, LinkedIn employees and usernames.
- Credential leaks.
Subdomains
This is the main strength of the tool, which is continually evolving and being revised to include new techniques. It currently returns more valid subdomains than any other tool or source, both paid and free.
- Passive subdomains’ extraction from 3rd parties indexed results like GitHub, Censys, Shodan, etc.
- Certificate transparency search.
- DNS bruteforcing with top wordlists.
- Advanced alterations and permutations.
- DNS records lookup.
- Subdomain extraction from TLS handshake.
- Websites and JS scraping subdomains search.
- Google Analytics ID relationships.
- Recursive processing option allowing in-depth lookup (both passive and active).
- Zone transfer checks.
- Subdomain takeover checks.
- DNS takeover checks.
- Cloud provider finder.
Websites
Websites are probably the biggest attack vector for most companies, so they require special attention and analysis. The tool performs:
- Websites resolution from active subdomains list.
- Websites resolution on non-standard ports.
- Web screenshoting.
- Favicon IP lookup.
- Nuclei templates-based scanner.
- Waf detection.
- Web fuzzing.
- CMS Scanner.
- Url extraction by passive and active methods.
- Vulnerability patterns search in urls collected.
- JavaScript analysis.
- Wordlists generation.
- URL sorting by extension.
- Passwords dictionary creation.
Hosts
Apart from websites, hosts are often a good source of vulnerabilities, so we need to know what is running on those juicy ports. For this task, reconFTW runs:
- IP info.
- CDN checker.
- WAF checker.
- Passive port scan.
- Active port scan.
- Searchsploit integration.
Vulnerabilities
This tool was not designed to exploit vulnerabilities, but given the amount of information collected, the need arose to review some configuration flaws or automate the detection of certain vulnerabilities on a massive scale. Currently, the following vulnerabilities can be exploited in an automated way:
- XSS.
- SQLi.
- CORS.
- Open Redirects.
- SSRF.
- CRLF.
- Broken link hijacking.
- LFI.
- SSTI.
- SSL checks.
- Command injection.
- Password spraying.
- Prototype pollution.
Extra
This tool does not claim to be the ultimate weapon to attack any target, but it does a great job in asset discovery and currently allows many people to consult the source code to know how to automate certain tasks or which tools to use.
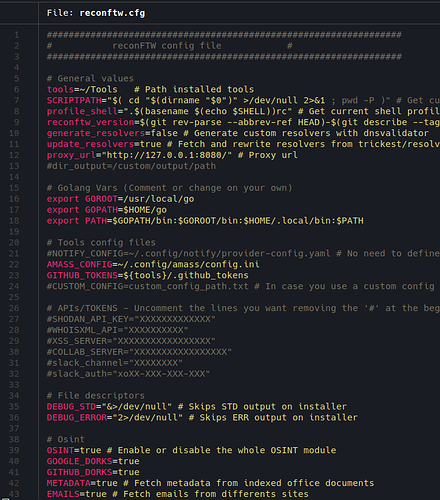
In addition, it can be deployed with Terraform and Ansible with AWS or run in a Docker container, and offers a configuration file to customize scanning to your needs, many different modes and flags. Some of the highlights of the customization in the config file are:
- Custom configuration files for some tools.
- Ability to define your own custom wordlists.
- Enable or disable any mode.
- Tools’s flags customization.
- Notification system and sending zipped results via Discord, Slack or Telegram.
- Distributed scanning with VPS.
- Data storage in MongoDB.
- Threading, timeouts and speed limits.
Configuration file overview
Conclusion
ReconFTW is used by many users around the world, from bug hunters to pentesters and ethical hackers, who help to improve this tool with their questions, suggestions or their tools for specific purposes that end up being integrated. So if you want to have a good recon process, learn more about it or help me to improve it, I invite you to try it and contact me if you need anything.